PuTTY is a terminal emulator and simple software for connecting to a Linux server on Windows.
This program supports several different protocols, including SCP, SSH, Telnet, and rlogin.
The name PuTTY does not have a special meaning, TTY is an abbreviation used in Unix for the word Teletype and the name of the terminal.
This program was originally written for the Microsoft Windows operating system, but it has been ported to several other operating systems. Official ports of this program exist for Unix-like operating systems.
Most Linux server users use the shell or command line to control their server, but the above program is one of the most famous software that provides this possibility for you.
Also, It has features such as the ability to save bookmarks for frequent connection addresses, the ability to connect to multiple servers simultaneously through separate windows, the ability to set up a proxy, and the ability to change connection settings at any time.
In addition, It provides features such as displaying terminal input and output simultaneously, creating secure tunnels (Secure Tunneling) to easily connect to servers that you do not have direct access to, and the ability to specify advanced network settings.
Most Linux server users use the shell, or command line, to control their server, but the above program is one of the most popular software that provides this possibility for you.
Now you can download the latest version of PuTTY software from the idownload.uno site.
Table of Contents
PuTTY: The Ultimate Guide to a Powerful SSH Client
In today’s interconnected world, remote access to systems is more important than ever. Whether you’re managing a server, troubleshooting issues, or simply administering remote devices, the need for secure and efficient communication is paramount. Enter PuTTY, a lightweight and reliable tool that has become one of the most widely used SSH (Secure Shell) clients in the tech community. With its ability to handle various network protocols and its minimalist interface, It provides an excellent solution for remote access and system administration tasks.
What is PuTTY?
It is an open-source software client for SSH (Secure Shell), Telnet, rlogin, and raw TCP connections. Originally developed by Simon Tatham for Windows, It is now available for Linux and other platforms as well. It allows users to securely connect to remote systems, typically servers, over a network. It provides the necessary interface for executing command-line operations on remote machines and is commonly used by system administrators, developers, and network engineers for tasks such as managing web servers, configuring routers, or performing remote troubleshooting.
Though it’s designed for SSH connections, It also supports several other protocols, making it a versatile tool for various remote network activities. It is well known for its simplicity, speed, and power, making it a go-to solution for both beginners and seasoned professionals.
Key Features of PuTTY
It offers a wide array of features that make it an ideal choice for remote access. Here’s an overview of its most important features:
1. SSH (Secure Shell) Protocol Support
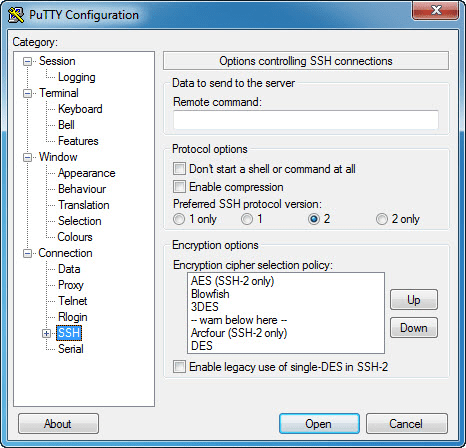
SSH is the most commonly used protocol for secure communication between a local machine and a remote server. It supports SSH 1 and SSH 2, with SSH 2 being the more secure and commonly used version. SSH ensures that all communication between the client and server is encrypted, making it ideal for sensitive tasks like system administration, managing databases, or accessing remote files.
2. Telnet and Rlogin Protocols
In addition to SSH, It also supports the older Telnet and rlogin protocols. These protocols are less secure than SSH but are still used in legacy systems where encryption is not necessary. While Telnet transmits data in plaintext, it can still be useful for certain non-critical applications.
3. Session Management
It allows users to store and manage multiple remote session configurations. You can create and save different session profiles, complete with specific settings like hostnames, port numbers, and connection preferences. This is especially helpful for system administrators who need to connect to different machines with varying configurations. Session profiles can be easily accessed and modified, which streamlines the connection process.
4. Key-Based Authentication
It supports key-based authentication, which provides a more secure method of logging into remote systems than traditional password authentication. By using an SSH key pair (a private key and a public key), users can authenticate themselves without the need to enter a password. This is particularly important for automating tasks and ensuring secure connections.
5. Port Forwarding
It allows users to forward ports between the local and remote machines. Port forwarding is useful for securing communication channels and accessing services (like web applications or databases) that are not directly exposed to the internet. With It , you can set up both local and remote port forwarding, enabling access to a variety of services through secure SSH tunnels.
6. Session Logging
It provides the option to log all activity during a session. This feature is useful for auditing, troubleshooting, or documentation purposes. The logs can be saved to a local file and reviewed later to track command execution, errors, or warnings during the session.
7. Customizable Interface
It features a minimalistic interface, but it’s highly customizable. Users can adjust the font, color scheme, and window appearance to match their preferences. This level of customization makes it easier for users to work comfortably, especially during long sessions.
8. X11 Forwarding
It can also be used to forward graphical applications from a remote system to the local machine. This feature, called X11 forwarding, allows users to run GUI-based applications over SSH, which is beneficial when managing remote Linux servers that require graphical interfaces.
Installation of PuTTY
Installing It is straightforward and can be done in a few simple steps. Here’s how you can get started:
1. Downloading PuTTY
It is available for Windows, Linux, and macOS, but it’s most commonly used on Windows systems. To download PuTTY for Windows, follow these steps:
- Go to the official website: https://www.putty.org/
- Click on the “Download” link to access the PuTTY download page.
- Download the appropriate version of the installer for your system (32-bit or 64-bit).
For Linux and macOS users, It can usually be installed from the default package manager.
2. Installing PuTTY on Windows
After downloading the installer file (typically named putty.exe), follow these steps to install It on your system:
- Double-click the installer to begin the installation process.
- Choose the destination folder for the installation or accept the default path.
- Complete the installation by following the on-screen instructions.
Once installed, you can launch It from the start menu or desktop shortcut.
3. Installing PuTTY on Linux
For Linux users, It can be installed using the package manager. On most Debian-based systems (such as Ubuntu), you can use the following commands:
sudo apt update
sudo apt install putty
For Red Hat-based systems, use:
sudo yum install putty
4. Installing PuTTY on macOS
On macOS, It can be installed using Homebrew:
brew install putty
Alternatively, you can download a precompiled binary for macOS from the official website or other trusted sources.
Common Use Cases for PuTTY
It is widely used in many different industries for a variety of purposes. Below are some of the most common use cases for It :
1. Remote Server Management
One of the primary uses of It is to manage remote servers, particularly Linux-based servers. System administrators use It to access servers via SSH, perform system updates, install software, troubleshoot issues, and monitor server health. It’s ability to securely connect to remote machines makes it an essential tool for managing servers, databases, and other critical infrastructure.
2. Network Administration
Network administrators rely on It for managing network devices, such as routers, switches, and firewalls, over SSH or Telnet. It’s versatile protocol support allows administrators to configure these devices remotely, saving time and enabling more efficient management of large networks.
3. Automated Scripts
It can be used to run automated scripts on remote systems. Many professionals use It in combination with PuTTY’s command-line utility, Plink, which allows for automated SSH connections. Plink can execute commands remotely, making it an invaluable tool for scheduled tasks and repetitive processes.
4. SSH Tunneling for Secure Connections
It is widely used for SSH tunneling, which allows users to secure their connection between local and remote systems. By using SSH port forwarding, users can create secure channels to access services (such as databases or web servers) that are behind firewalls or NAT (Network Address Translation). SSH tunneling with It helps protect data transmission and bypass network restrictions.
5. Troubleshooting and Diagnostics
It is an essential tool for troubleshooting network and server issues. IT professionals use It to connect to remote systems and run diagnostic commands like ping, traceroute, and netstat. These commands help diagnose network problems, detect security vulnerabilities, and troubleshoot server issues.
Advantages of Using PuTTY
Here are some of the key advantages of using It for remote access:
1. Open Source and Free
It is an open-source project, which means that it’s free to use and regularly updated. There are no licensing costs or limitations on usage, making it an affordable and reliable choice for individuals and organizations alike.
2. Small and Lightweight
It is known for its small file size and minimalistic design. Despite being lightweight, it doesn’t sacrifice functionality. It’s fast, doesn’t consume many system resources, and is easy to install and use.
3. Versatile Protocol Support
With support for SSH, Telnet, rlogin, and raw TCP, It is a versatile tool that can handle various types of remote network connections. This makes it suitable for a broad range of applications across different operating systems and network environments.
4. Security
It provides strong encryption for remote connections, ensuring that data transmitted between the client and server is secure. By using SSH key-based authentication and port forwarding, It helps users protect their remote communications from unauthorized access.
5. Customizability
It offers a high degree of customizability. Users can tailor the interface, color schemes, font settings, and more. This allows users to optimize the It interface to their specific needs and preferences, enhancing their overall experience.
Disadvantages of Using PuTTY
While It is an excellent tool for many use cases, it’s not without its limitations:
1. No Native GUI for SSH Key Management
It does not have a built-in graphical user interface (GUI) for managing SSH keys, which can make key management more complicated. However, there are third-party tools, like PuTTYgen, that can be used to generate and manage keys.
2. Windows-Centric
It was initially designed for Windows, and although it has been ported to Linux and macOS, its Windows-centric nature means that some features might not be as polished on other operating systems. Users on non-Windows platforms might experience some limitations.
3. No Built-in File Transfer
While It supports SSH and remote terminal access, it lacks a built-in file transfer mechanism. Users who need to transfer files between their local and remote systems should use additional tools, such as PSCP (PuTTY Secure Copy) or WinSCP.
PuTTY Features
- Ability to simulate computer and program consoles
- Ability to use it on different operating systems
- A complete tool for professional users and network experts
- Control system resources and protocols
- Support for PSCP as an SCP client to copy files using the command line
- Support for PSFTP as an SFTP client with similar functionality to FTP
- Support for PuTTYtel as a special Telnet client
- Open source software
- Save bookmarks of frequent connection addresses
- portable PuTTY
Frequently Asked Questions (FAQs) About PuTTY
1. What is PuTTY?
It is an open-source software that allows users to connect to remote computers over various protocols, including SSH (Secure Shell), Telnet, rlogin, and raw TCP. It’s primarily used for securely managing remote servers, especially Linux-based systems, from a local computer. It is most commonly used for secure shell (SSH) connections, enabling users to execute commands on a remote machine.
2. Is It free?
Yes, PuTTY is completely free and open-source. Users can download and use it without any licensing fees or restrictions. As an open-source project, it’s continuously updated and improved by its community of developers.
3. What platforms can I use PuTTY on?
It was originally designed for Windows, but it is also available for other platforms like Linux and macOS. While Windows users can download the PuTTY installer, Linux users can usually install It through their distribution’s package manager (e.g., apt-get for Ubuntu). On macOS, It can be installed via Homebrew or through other methods.
4. How do I install It ?
To install It , follow these steps:
- For Windows:
- Go to the official PuTTY website https://www.putty.org/.
- Download the Windows installer or the standalone
.exefile (e.g.,putty.exe). - Follow the installation instructions to install PuTTY on your machine.
- For Linux:
- Debian-based distributions (e.g., Ubuntu): Run the command
sudo apt-get install puttyin the terminal. - Red Hat-based distributions (e.g., CentOS): Run the command
sudo yum install putty.
- Debian-based distributions (e.g., Ubuntu): Run the command
- For macOS: Install PuTTY via Homebrew using the command
brew install putty.
5. What is SSH and why is it important in PuTTY?
SSH (Secure Shell) is a cryptographic network protocol used for securing remote connections. It supports SSH, which ensures that all data sent over the connection is encrypted, making it much more secure than other protocols like Telnet or rlogin. SSH is crucial for securely administering servers, accessing cloud platforms, and transferring sensitive data across a network.
6. Does It support SSH key-based authentication?
Yes, It supports SSH key-based authentication, which provides a more secure method of logging into remote systems than password-based authentication. Users generate an SSH key pair (private and public keys), and the public key is placed on the remote server. When connecting via It , the private key is used for authentication, eliminating the need for a password.
You can use PuTTYgen to generate SSH keys on Windows and configure key-based authentication.
7. How do I save session configurations in PuTTY?
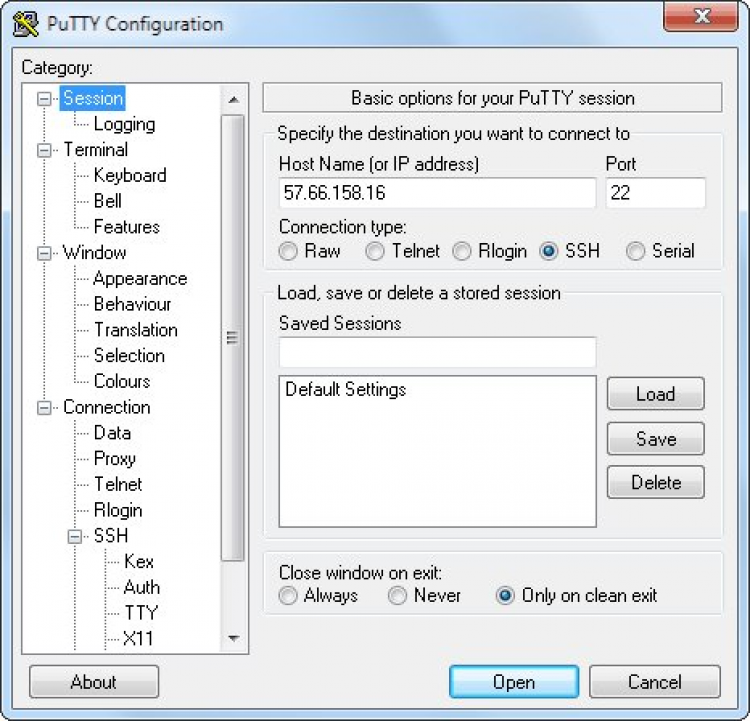
It allows you to save your session configurations so you don’t need to re-enter connection details every time you connect to a remote server. Here’s how you can save a session:
- Open It and enter your hostname or IP address of the remote system.
- Under “Saved Sessions,” type a name for your session (e.g., “MyServer”).
- Click Save to store the configuration.
Once saved, you can simply select the session from the list and click Load to quickly connect to the remote server.
8. How do I change the appearance of It’s terminal?
It allows users to customize the appearance of the terminal, including font size, color schemes, and window settings:
- Open PuTTY and load the desired session.
- In the sidebar, go to Window > Appearance.
- Click Change to modify the font style and size.
- You can also go to Colors to adjust the color settings of the terminal window.
9. Can PuTTY be used to transfer files?
It itself doesn’t have a built-in file transfer feature, but it works in conjunction with tools like PSCP (PuTTY Secure Copy) and WinSCP for file transfers over SSH.
- PSCP is a command-line tool that allows users to transfer files to and from remote systems.
- WinSCP is a GUI-based tool that also uses SSH for secure file transfers.
Both of these tools are available for free and can be downloaded from the website.
10. What is PuTTYgen and how do I use it?
PuTTYgen is a tool that comes with It and is used to generate SSH key pairs (public and private keys) for authentication. Here’s how you can use it:
- Open PuTTYgen (you can find it in the same folder as It ).
- Click Generate to create a new key pair.
- Move your mouse randomly over the blank area to generate entropy.
- Once the keys are generated, you can save the public key (to place on the remote server) and the private key (to keep on your local machine).
- You can then configure It to use the private key for SSH authentication when connecting to the remote server.
11. Can It be used for port forwarding?
Yes, It allows you to configure SSH port forwarding. Port forwarding is useful when you want to securely access services running on remote systems (such as databases or web servers) through an encrypted SSH tunnel. You can set up both local and remote port forwarding:
- Open It and navigate to the Connection > SSH > Tunnels section.
- Select the type of port forwarding (local or remote) and specify the source and destination ports.
- Click Add to add the port forwarding rule, and then connect to the remote server.
12. Does It support X11 forwarding?
Yes, It supports X11 forwarding, which allows you to run graphical applications on a remote machine and display them locally on your computer. To enable X11 forwarding:
- In It , go to Connection > SSH > X11.
- Check the box for Enable X11 forwarding.
- Connect to the remote system.
Note: You’ll need an X server running on your local machine (e.g., Xming for Windows) to display the graphical applications.
13. What is the difference between SSH, Telnet, and rlogin in PuTTY?
It supports multiple protocols, including:
- SSH: A secure and encrypted protocol for remote login and command execution. SSH is the most commonly used protocol and is recommended for security.
- Telnet: An older protocol that transmits data in plaintext, which means it’s not secure. Telnet is mostly obsolete and should only be used for legacy systems.
- rlogin: Another older protocol used for remote login, also unencrypted and insecure. Like Telnet, rlogin should be avoided in favor of SSH.
For security, it is recommended to always use SSH instead of Telnet or rlogin.
14. Can I run automated scripts with PuTTY?
Yes, you can automate tasks and run scripts remotely using It’s command-line utility, Plink (PuTTY Link). Plink allows you to execute commands on a remote server without manually opening a It session.
For example, you can use Plink in a batch file or a script to connect to a remote server and run commands automatically:
bashCopyplink -ssh username@hostname -i private_key.ppk "your_command_here"
This is useful for automating server management tasks and scheduled jobs.
Screenshots
How to Use Putty to SSH on Windows
Conclusion
It remains one of the most popular and reliable tools for remote access, offering users the ability to connect securely to remote systems, manage networks, and perform administrative tasks across various platforms. Its support for multiple protocols, session management, key-based authentication, and SSH tunneling makes it an indispensable tool for many professionals.
Although It has a minimalistic design and lacks some advanced features found in other solutions, its lightweight nature, security, and versatility ensure it remains an essential part of any IT professional’s toolkit. Whether you’re an experienced system administrator or a casual user, It offers a straightforward and reliable solution for remote access and server management.
Download
Source
https://www.putty.org